HIPAA Compliance Consulting Services
From Assessment to Implementation
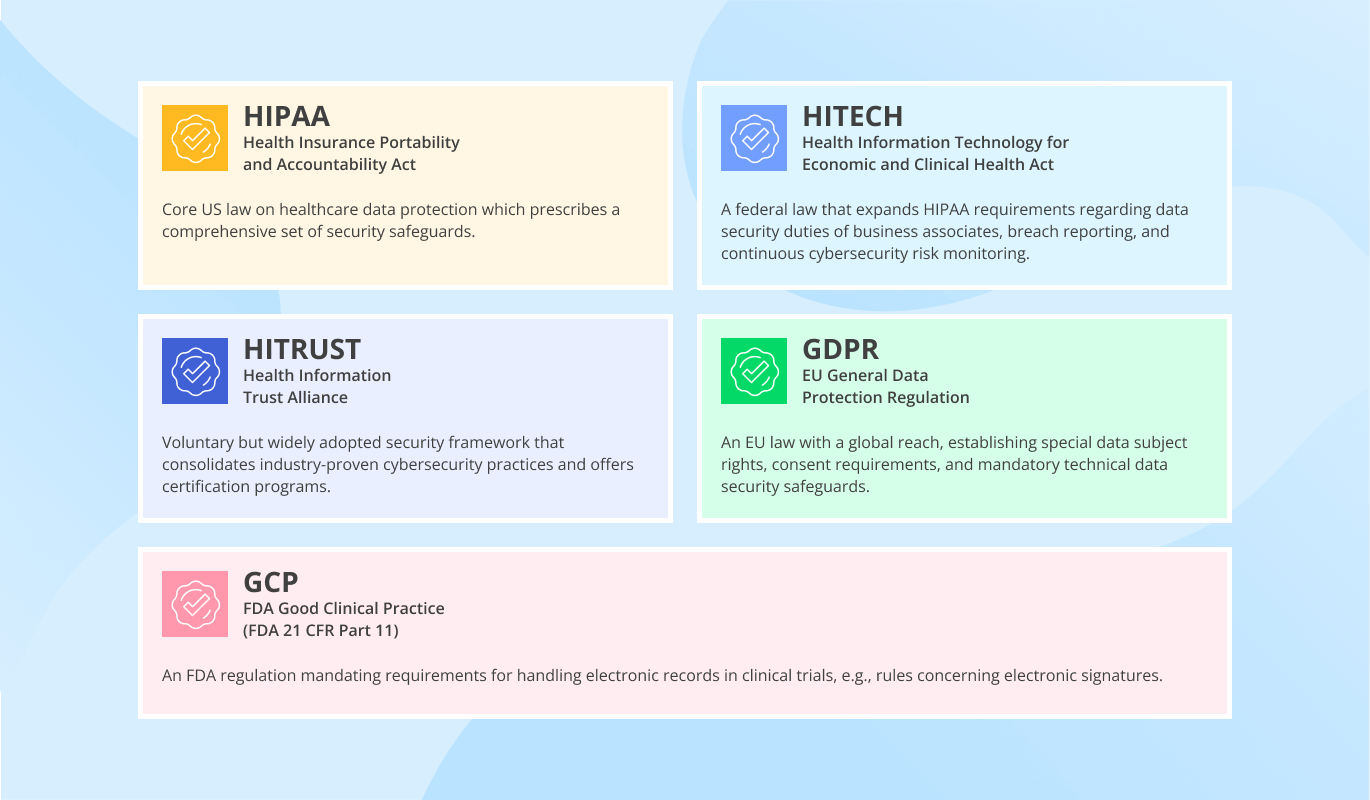
Since 2005 in healthcare IT and since 2003 in cybersecurity, ScienceSoft offers remote consulting to help healthcare companies, medical software and device manufacturers achieve HIPAA compliance.
HIPAA compliance consulting embraces evaluating a company’s security policies, procedures and controls for PHI protection, recommendations on fixing deviations from HIPAA requirements, and developing HIPAA-compliant software.
Who We Serve
Healthcare providers
- Hospitals.
- Clinics.
- Nursing homes.
- Rehabilitation facilities.
- Medical labs, and others.
Healthcare software product companies and medical device manufacturers
- EMR and EHR vendors.
- Telemedicine software vendors.
- Medical diagnosis software companies.
- VR and AR healthcare solution providers.
- Digital therapeutics vendors.
- SaMD vendors.
- Internet of medical things (IoMT) companies, and others.
The Scope of Our HIPAA Consulting Services
PHI risk analysis and mitigation strategy design
- Determining the assets used in operations with PHI, employees and business associates having access to PHI.
- Identifying and documenting vulnerabilities, potential threats, and their impact.
- Evaluating existing security measures.
- Developing PHI risks mitigation strategy.
HIPAA policies and procedures review and improvement
- Evaluating and enhancing PHI access, storage, transmission, disposal, and backup policies.
- Assessing and improving incident response and breach notification process.
- Evaluating and helping establish continuous monitoring and assessment of PHI security.
IT security gaps detection and remediation
- Vulnerability scanning.
- Penetration testing.
- Software source code review.
- Software architecture review.
- Recommending and implementing corrective measures for security flaws endangering PHI.
HIPAA awareness promotion
- Evaluating your staff’s and business associates’ knowledge of HIPAA provisions.
- Recommendations for efficient HIPAA training process.
HIPAA-compliant software design
- Choosing or helping to migrate to a HIPAA-compliant platform.
- Designing secure software architecture.
- Advising on secure coding best practices.
Recommendations on securing IT networks against PHI breaches
- Advising on secure network architecture, optimal placement and configuration of firewalls, anti-malware, IDS/IPS.
- Guidance on security information and event management (SIEM) implementation.
- Helping establish identity and access management.
Our Clients Say
ScienceSoft provided an excellent level of service in:
- Code assessment of our existing healthcare application for life science research;
- Consulting on best practices and standards in healthcare and life science software development;
- Research on medical devices (functionality, safety classes, registration, etc.) to be used in the future project;
- Preparation activities for a planned platform development project: architecture planning, verification planning, software development lifecycle processes, risk management processes.
They bring top quality talents and deep knowledge of IT technologies and approaches in accordance with ISO13485 and IEC62304 standards.
Sergey Shleev, Prof. Dr. Department of Biomedical Science, Malmo University
Deliverables
Depending on the consulting service option you choose, you get reports and recommendations that you can use to prevent non-compliance, implement a HIPAA compliance measures or develop HIPAA-compliant software. In case of an OCR audit, they will serve as a tangible proof of your efforts to protect PHI. Here are some sample deliverables for different service options.
Assessment deliverables
- PHI security risk assessment report.
- Network topology diagrams.
- Vulnerability assessment and pentesting reports with description and prioritization of found vulnerabilities and remediation recommendations.
- Software architecture and source code review reports on identified flaws, endangering PHI, and remediation steps.
- (for software companies) Development infrastructure description and its assessment against HIPAA requirements.
Recommendation deliverables
- Remediation plans to address existing compliance gaps.
- PHI security risk mitigation plan.
- Designs for HIPAA-compliant IT infrastructure and software architecture.
- A roadmap to migrate to a HIPAA-compliant infrastructure.
- Overview of HIPAA-compliant platform providers with recommendations.
Why ScienceSoft
- Since 2005 in healthcare IT and since 2003 in cybersecurity.
- Quality-first approach and mature quality management system confirmed by ISO 13485 and ISO 9001 certifications.
-
ISO 27001-certified security management based on evergreen policies, well-implemented processes, and advanced technology and skills.
Choose Your Service Option
Consultation on HIPAA-compliant software development
- Cost and ROI estimation for your development project.
- Planning HIPAA-compliant software development and launch.
- Planning the DevSecOps strategy.
- Advising on secure architecture, coding practices, and development tools (libraries, frameworks, etc.).
Design and implementation of HIPAA compliance program or specific compliance measures
- Designing security policies and procedures required by HIPAA.
- Outlining a set of measures for PHI protection (e.g., multi-factor authentication, PHI encryption, antimalware etc.).
- Establishing HIPAA training process for your staff and business associates.
HIPAA compliance assessment
- Impartial review of HIPAA policies and procedures.
- Security testing of software and IT infrastructure involved in operations with PHI.
- Recommendations to fix deviations from HIPAA requirements to ensure compliance and prepare for OCR audits.
HIPAA Compliance Consulting: Sample Process
The consulting process we follow depends on the type of business, specific compliance needs, and the required service scope. Here is a sample process:
1
Analyzing the existing HIPAA compliance program or existing security policies and measures aimed at PHI breach prevention, notification and remediation.
2
Conducting interviews with the staff to assess their HIPAA awareness.
3
Evaluating the security of IT infrastructure and software operating with PHI (vulnerability assessment, pentesting, software architecture or source code review, etc.), providing reports on the performed activities with remediation guidance for detected security gaps.
4
Recommendations from HIPAA consultants on developing and implementing the missing policies and procedures and IT security controls for PHI protection.
HIPAA Compliance Challenges We Handle
Challenge #1
It may be difficult to build a team that can assess and enable both administrative and technical safeguards envisaged by HIPAA, as it requires expert knowledge of both healthcare business processes and IT environment.
Solution
Challenge #2
To be HIPAA-compliant, a company must not only develop and implement security policies and procedures on PHI protection, but also timely fix security gaps at administrative and technical levels.